While Rwanda’s ambassadors are successful in doing a lot of good work worldwide to improve Rwanda’s image and relations with foreign governments - all in the interest of much needed development - Rwanda’s reputation on the Internet is effectively going just the opposite way: From bad to worse, and even critical. Why? Well, the answer is simple, though somewhat technical. It can be put in only one word: Spamming.

While Rwanda’s ambassadors are successful in doing a lot of good work worldwide to improve Rwanda’s image and relations with foreign governments - all in the interest of much needed development - Rwanda’s reputation on the Internet is effectively going just the opposite way: From bad to worse, and even critical. Why?
Well, the answer is simple, though somewhat technical. It can be put in only one word: Spamming.
On the Internet, that basically refers to the activity of sending out loads of junk e-mails, often to randomly selected e-mail accounts.
Whether they are begging, advertising more or less fake products or trying to lure money from the recipients in other ways or whatever else they contain - it is a criminal activity!
Even worse: Viruses operating in similar ways are used to steal things like bank- and credit card information.
As a consequence, Internet watchdog organizations have long been setting traps to detect that kind of thing.
So whenever they detect attempted or suspected spamming, they list the point of origin of such traffic in lists called RBL or something similar.
The -BL stands for: Blocking List or BlackList. And whereas getting on an RBL is easy, the thing about getting off it again depends on the policies of the different RBL information providers.
So what does that have to do with Rwanda, and how does it all really work?
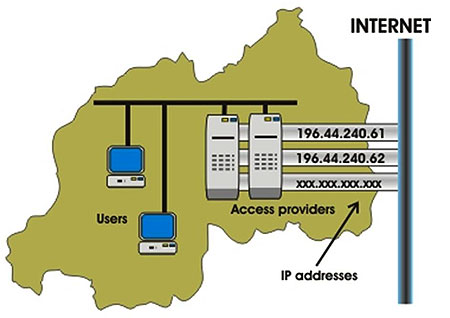
Well, it all starts and ends with the Internet access providers. Here in Rwanda, that means MTN, Rwandatel and now also Tigo.
Every physical connection to the Internet, used by the access providers, is assigned one or more unique numbers - the so-called IP addresses.
Thus an IP address is an address on the Internet - pretty much like a Po-Box number. And every country worldwide has a number of such addresses assigned for its use.
Computers are generally polite creatures. When two computers exchange an e-mail, they first greet each other by saying hello.
After saying hello, the sending computer asks the one on the receiving end if it will accept an e-mail sent to this or that e-mail address.
But now, an increasing number of e-mail servers worldwide are checking to see if the point of origin (the IP address) is listed in one blocking list or another, before accepting to receive anything. And if that is the case, the receiving mail server just might reply: "JunkMail rejected - [196.44.240.62] is in an RBL, see”.
As a result, there is just no way to deliver the e-mail. Why? Because IP address 196.44.240.62 is blacklisted worldwide!
The IP address 196.44.240.62 belongs to MTN. It is used (together with 196.44.240.61) for Internet access by customers using wireless (GSM) modems.
In this case, the reply was received from an e-mail server at a hosting service provider in USA. And 196.44.240.62 is currently found on at least one third of all the main blocking lists.
It should be added, that the response from the mail server mentioned above, was received while the number was not listed in the CBL. But the CBL is only one list - there are numerous others, so obviously it could be found elsewhere last month...
How does it all happen?
Spamming and other illicit Internet activities can be generated using so-called vulnerable mail servers. That typically means mail servers installed and maintained by less competent IT technicians, so they are easy to break into by hackers.
But between the mail server and the actual Internet, there is usually also a little something called a firewall. Its job is to make hacking into servers and computers on the network difficult. Hence the name - it is there for protection.
But that one alike is not really all that easy to install and configure correct. And while a firewall can protect against hacking from the outside, it has no control of what’s going on the network behind it.
And worst of all - it does not even take a mail server to send e-mails. That can be done from any computer connected to the Internet. It takes only a small piece of program code, which is often distributed as a virus.
Still - depending on how the Internet Access Provider (IAP) configures routers and firewalls. But nevertheless, this seems to be the real reason behind the blacklisting of the IP addresses reported above.
Still - what does all that have to do with Rwanda’s reputation?
Well, quite a lot, actually. It all means that on the Internet, Rwanda’s reputation - concerning e-mail traffic - is bad. Very bad indeed. It is not the result of anyone manipulating the blacklists or reputation reports.
They are all generated automatically, based on actual traffic and virus distribution statistics. And it is not just a problem for MTN only.
A brief glance through reports show, that at least half of all IP addresses used by Rwandan IAPs, are on one or more blacklists because of spamming. And every IP address has its country linked to it.
More and more users worldwide rely increasingly on the Internet as their primary source of information and channel of communication and business.
And it becomes more and more widely recognized that a country’s reputation can effectively not be much better than the reputation of the activities on its connected networks, i.e.: The use of its IP addresses.
And it does look bad…
And it is not only a matter of reputation. The present state of affairs also causes obstacles for the use of the Internet from Rwanda in general.
When mail servers refuse to receive legitimate e-mails, just because they are sent from Rwanda, and some websites even refuse to respond after checking with the same listings, the situation is really getting critical.
It’s an obstacle to business, communication and development. And moreover - whether caused by viruses or more specifically orchestrated targeting of individual mail servers on the networks inside the country, it all also generates a lot of waste traffic on the network lines, which are already far too small and slow for providing anything even close to today’s demand for Internet connection speed.
So - What can be done about it?
Getting an IP address on anyone of those lists is really easy. It happens automatically every time spamming or other related, illicit activities are detected from any IP address.
Many of the lists also automatically delete the listing after a while; some offers even instant deletion upon request. But getting off one list or another does not solve the problem.
It does not stop the spamming. And when the illicit traffic continues, the IP addresses get listed again. And again, and again... And that creates a very low score on the reputation index.
Ultimately it will result in Rwandan IP addresses being permanently listed without any chance of ever getting off those lists again, if nothing is done to solve the problem.
Merely requesting deletion from the lists today will not solve anything. Quite to the contrary. Spammers and hackers are always on the prowl for vulnerable servers and other opportunities to carry out their illicit activities.
So when the IP addresses they use get repeatedly re-listed (as it happens now), the whole situation effectively just keeps getting worse and worse.
Still, it all starts and ends with the Internet access providers. They are ultimately responsible for the use of their IP addresses. And there is basically two strategies they can deploy to solve the problem.
One being crude, primitive, unprofessional and absolutely wrong. Especially as it will also result in the Internet access services to become of even poorer quality than they already are.
And here’s why: The primitive strategy is the one of simply closing more and more communication ports in routers and firewalls, until the problem cease to show outside Rwanda. But that neither cleans up the internal networks, nor does it in any way improve the quality of the access service. Quite to the contrary.
In fact, some of the access providers’ technicians already seem to have tried that in a feeble attempt to establish some network security. As a result, Internet users in Rwanda - connecting through MTN or Rwandatel - are denied even their most basic rights to e-mail privacy.
Especially if they use the very popular Microsoft Outlook program to handle e-mails accounts on domains hosted outside Rwanda. Simply because the communication ports required for transferring the mails on a so-called secure socket layer (SSL) have been closed.
Apparently by some people without too much idea what they are used for in the first place. (SSL provides a data encryption, which makes it difficult for hackers to steal e-mail information).
Just try to use the also very popular gmail with Outlook. It won’t work. Not in Rwanda. As a result, many e-mail accounts used by people in Rwanda are easily compromised by hackers and other cyber criminals.
Not good. In fact, opening the ports required for secure mail transmissions would be a noticeably effective improvement of the access services quality - and it wouldn’t cost the providers a thing, to show that concern for their customers!
The other strategy, on the other hand, is far more thorough and demanding on skills. But if deployed in the right way, it will ultimately identify the real causes and sources of the problems. And it might even result in better access services.
That strategy involves analysis of an almost unfathomable amount of so-called server log files (that’s where the computers, providing e-mail and other services, keep records of the traffic).
It involves also fine-tuning of routers, firewalls and servers, based on the information found in those logs.
Plus installation of spam traps and filters, along with implementing a safe strategy concerning Internet access for computers, from where spamming is generated by viruses.
That’s the tough and tedious, but professional way to go. Deployed right, it will ultimately identify and pacify the sources of illicit Internet traffic from Rwanda.
It can be done, though it will take some real efforts. But it’s not even that much of an enormous job, if done right. After all, there’s still a limited number of IP addresses in use in Rwanda, and a limited number of servers on the networks.
But it requires some serious brain work, along with some dedication to actually getting to the bottom of the problem.
Possibly even cooperation between telecom rivals as well. It will be interesting to see what the Internet access providers will actually care to do about it.
One of the blocking list information providers (Composite Blocking List) reports:
IP Address 196.44.240.62 is currently listed in the CBL.
It was detected at 2010-02-09 18:00 GMT.
It has been relisted following a previous removal at 2009-12-17 02:35 GMT
ATTENTION: At the time of detection, this IP was infected with, or NATting for a computer infected with a high volume spam sending trojan - it is participating or facilitating a botnet sending spam or spreading virus/spam trojans.
ATTENTION: If you simply repeatedly remove this IP address from the CBL without correcting the problem, the CBL WILL eventually stop letting you delist it and you will have to contact us directly.
This is the mega-d spamBOT
You MUST patch your system and then fix/remove the trojan. Do this before delisting, or you’re most likely to be listed again almost immediately.
And...
IP Address 196.44.240.61 is currently listed in the CBL.
It was detected at 2010-02-09 19:00 GMT.
It has been relisted following a previous removal at 2009-12-16 22:27 GMT
ATTENTION: At the time of detection, this IP was infected with, or NATting for a computer infected with a high volume spam sending trojan - it is participating or facilitating a botnet sending spam or spreading virus/spam trojans.
ATTENTION: If you simply repeatedly remove this IP address from the CBL without correcting the problem, the CBL WILL eventually stop letting you delist it and you will have to contact us directly.
This is the grum spamBOT
And another IP address used by MTN, is reported like this:
IP Address 196.44.240.198 is currently listed in the CBL.
It was detected at 2010-02-09 16:00 GMT.
...this IP is infected with/emitting spamware/spamtrojan traffic and needs to be fixed.
Copyright © 2010 Jan Kirstein


